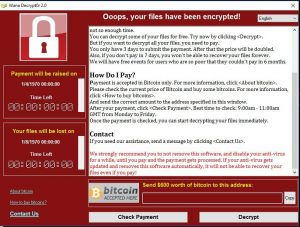
The Department of Information and Communications Technology (DICT), through Secretary Rodolfo A Salalima and Assistant Secretary Allan S Cabanlong confirms that a global ransomware attack is currently in progress. The sophisticated ransomware, known as ‘Wanna Cry’ or ‘Wanna Decryptor’, exploits a vulnerability in Microsoft’s Windows operating system.
This malware is designed to spread laterally on a network by gaining unauthorized access to the IPC$ share on network resources on the network on which it is operating. It is also believed that this ransomware is spread through phishing emails, malicious adverts on websites, and questionable apps and programs. Users are advised to be extremely cautious in their online activities.
Recommended Steps for Prevention
- The first and most important piece of guidance is to immediately deploy the security update associated with Microsoft Security Bulletin MS17-010<https://technet.microsoft.com/en-us/library/security/ms17-010.aspx>, if you have not done so already. Those that have automatic updates enabled or have deployed this update are already protected from the vulnerability these attacks are trying to exploit.
- Manage the use of privileged accounts. Implement the principle of least privilege. No users should be assigned administrative access unless absolutely needed. Those with a need for administrator accounts should only use them when necessary.
- Configure access controls including file, directory, and network share permissions with least privilege in mind. If a user only needs to read specific files, they should not have write access to those files, directories, or shares.
- Disable macro scripts from Microsoft Office files transmitted via e-mail. Consider using Office Viewer software to open Microsoft Office files transmitted via e-mail instead of full Office suite applications.
- Scan all incoming and outgoing e-mails to detect threats and filter executable files from reaching the end users.
- Enable strong spam filters to prevent phishing e-mails from reaching the end users and authenticate in-bound e-mail using technologies like Sender Policy Framework (SPF), Domain Message Authentication Reporting and Conformance (DMARC), and DomainKeys Identified Mail (DKIM) to prevent e-mail spoofing.
- Ensure anti-virus and anti-malware solutions are set to automatically conduct regular scans.
- Develop, institute and practice employee education programs for identifying scams, malicious links, and attempted social engineering.
- Have regular penetration tests run against the network. No less than once a year. Ideally, as often as possible/practical.
- Test your backups to ensure they work correctly upon use.
Recommended Steps for Remediation
- Contact the Philippines National Computer Emergency Response Team (NCERT) of the DICT and CICC for law enforcement escalation by sending an email to: [email protected]. We strongly encourage you to contact the NCERT / CICC upon discovery to report an intrusion and request assistance. Maintain and provide relevant logs.
- Implement your security incident response and business continuity plan. Ideally, organizations should ensure they have appropriate backups so their response is simply to restore the data from a known clean backup.
Defending Against Ransomware Generally
Precautionary measures to mitigate ransomware threats include:
- Ensure anti-virus software is up-to-date.
- Implement a data back-up and recovery plan to maintain copies of sensitive or proprietary data in a separate and secure location. Backup copies of sensitive data should not be readily accessible from local networks.
- Scrutinize links contained in e-mails, and do not open attachments included in unsolicited e-mails.
- Only download software – especially free software – from sites you know and trust.
- Enable automated patches for your operating system and Web browser.
Furthermore, The DICT, through its Office for CyberSecurity and Enabling Technologies is currently looking for new innovative ways to do Isolation. Gone are the days of Traditional Isolation like segragation of networks – airgap. This technique is believed to help protect our system from cyber threats including ransomware.
For further information and support, please contact DICT at 920-0101 LOC 1200; email at [email protected] or visit https://www.facebook.com/CICC.PH. Future updates will be provided as more information becomes available.
References
- Malwarebytes LABS: “WanaCrypt0r ransomware hits it big just before the weekend
- Malwarebytes LABS: “The worm that spreads WanaCrypt0r”
- Microsoft: “Microsoft Security Bulletin MS17-010”
- Forbes: “An NSA Cyber Weapon Might Be Behind A Massive Global Ransomware Outbreak”
- Reuters: “Factbox: Don’t click – What is the ‘ransomware’ WannaCry worm?”
- GitHubGist: “WannaCry|WannaDecrypt0r NSA-Cybereweapon-Powered Ransomware Worm”
